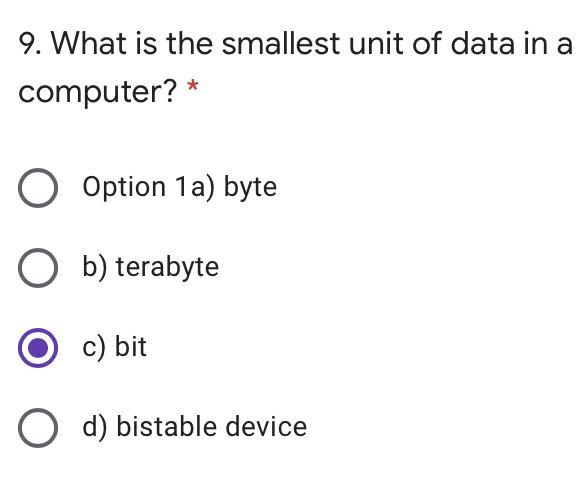
Answers
Explanation:
(A) trust me I'm computer hecker experts
Related Questions
You are running the Chrome Web browser and try to open a Web site when you are prompted for login credentials. What TCP/IP model layer is at work that requires you to logon to the Web site
Answers
Considering the situation described above, the TCP/IP model layer that is at work that requires you to log on to the Web site is known as the "Application layer."
The application layer, otherwise known as the abstraction layer, is defined in the Internet Protocol Suite (TCP/IP) and the OSI model.
Also, the application layer determines the shared communications procedures and interface modes utilized by the hosts in a communications network.
Some of the common examples of application layer include the following:
Hypertext Transfer Protocol (HTTP),File Transfer Protocol (FTP),Domain Name System (DNS), etc.Hence, in this case, it is concluded that the correct answer is "Application layer."
Learn more here: https://brainly.com/question/25278036
How were these isometric letters created?
Answers
Answer:
Using the 3D Extrude & Bevel effect.
Explanation:
I just took the test, I got a 100.
to determine the highest number in a range of numbers, click insert function box in the formula bar to display the insert function dialog box, then select ____.
Answers
Functions in Excel are used to perform several arithmetic and logical operations.
The text that completes the statement is MAX
From the question, we understand that you want to determine the highest number in a given range of numbers.
This is done using the MAX function.
i.e. after the insert function box has been selected, the formula to use is the MAX function.
Hence, the complete statement is:
Click insert function box in the formula bar to display the insert function dialog box, then select MAX.
Read more about Excel functions and formulas at:
https://brainly.com/question/20497277
Translate "God" Into Italian
Answers
Answer:
Dio is god in Italian
Explanation:
hope it helps
Answer:
Dio = God in Italian
u What is the full form of DRAM? a) Dynamic Remote Access Memory b) Dynamic Random-Access Memory c) Dependent Remote Access Memory d) Dependent Random-Access Memory
Answers
Answer:
B
Explanation:
Dynamic Random-Access Memory
What is the advantage of learning through story compared to learning through personal experience?
A.
stories are “more real” than personal experience
B.
stories are easier to remember than personal experiences
C.
stories have no rules to follow
D.
you can learn from countless other lifetimes through stories
This is game design
Answers
Answer:
I think the answer would be D
Explanation:
it just seems to make the most sense
Answer:
Is D
Explanation:
Stories open doors which ususally take time to open and to explore in real life, the same thing happens when you use a book to do your homework. You use the book to get information which you don't know. The same is with reading stories, stories can be helpful since they can talk about a characters life mistakes, and experiences that the character has gone throught their life, which usually might be helpful on real life.
The __________ algorithm takes the ciphertext and the secret key and produces the original plaintext
Answers
We _____ information about space. For example, while reading a textbook, we encode the place on a page where certain material appears.
Answers
Answer:
Extremes is the answer for the blank.
Explanation:
can you still receive messages on messenger from a person when you deleted the conversation with them? (But not blocked them)
Answers
The data cache is where the data read from the database data files are stored _____ the data have been read or _____ the data are written to the database data files.
Answers
Data is known to have cache. The data cache is where the data read from the database data files are stored after the data have been read or before the data are written to the database data files.
Cached data are simply called too be the information that is saved on one's computer or mobile devices after a person have visited or accessed a website.
A lot of Developers often make use of cached data to boast their online experience. A considerable number of consumers often want a website to load within two and three seconds.
Learn more from
https://brainly.com/question/23708299
Helppppppp pleaseeeewweeweee
Answers
Answer:
D
Explanation:
Applications software (also called end-user programs) include such things as database programs, word processors, Web browsers and spreadsheets
Python converts your code into bytecode when you run your program. This process is an intermediate step in a process called.
Answers
Python first compiles your source code (. py file) into a format known as byte code . Compilation is simply a translation step and byte code is a lower level and platform-independent representation of your source code
Python converts your code into bytecode when you run your program. This process is an intermediate step in a process called Compilation.
The line of code returns the ASCII code.
ASCII, has the full form American Standard Code for Information Interchange. It consists of a 7-bit code in which every single bit represents a unique alphabet.
Python is a high-level computer programming language. It is dynamically used.
First, it does a compilation for a file with the extension `.pyc`
Python converts your code into bytecode when you run your program. This process is an intermediate step in a process called Compilation.
Learn more about Python code here:
https://brainly.com/question/34746850.
#SPJ3
4.10.4 Inventory codehs python
i have no idea on how tp fix this, pls help:(
Answers
Answer:
between line 23 and 24, add:
if num > 0:
(and indent the next line)
Explanation:
You want to suppress the "Now we have 0 left" message, and an additional if statement will do that for you.
In this exercise we want to use computer and python knowledge to write the code correctly, so it is necessary to add the following to the informed code:
if num > 0:
Want to suppress the "Now we have 0 left" message, and an additional so for that is necessary to put between line 23 and 24, the code:
if num > 0:
See more about computer at brainly.com/question/950632
translate ¨friends¨ into spanish
Answers
Answer: I hope this is helpful
Explanation:
Friends in Spanish is Amigo- masculine aka male ,noun.
Friend in Spanish is Amiga- feminine aka Female , noun
Friends- trusted and caring person
How to edit an existing recipient list? class 9 for(3 marks)
Answers
Answer:
(Archives) Microsoft Word 2003: Mail Merge: Working with the Recipient List
Last updated Monday, Aug. 31, 2020, at 10:35 a.m.
This article is based on legacy software.
For a successful Mail Merge, you will need to establish a recipient list, also referred to as the data source. This contains the information that will vary with each record, such as names or identification numbers. If you are creating a mailing list, for example, names and addresses will be included in your data source.
You can either create a new data source or use a pre-existing source, such as your Outlook Contacts. You may also wish to alter the entries in your data source without having to open it, change the appropriate entries, and then save the changes. Mail Merge allows you to specify which individual entries you want to include as well as add and delete data document entries and fields.
Creating a New Data Source
Before creating the data document, take a moment to plan out the information you want to include. While creating your data document, you can add or remove fields to tailor the document to suit your needs. Creating a new data source is an option in the third step of the Mail Merge Wizard.
what is draft pls help me
Answers
Answer:
draft like as a rough draft it pretty much a set were you can play and the do the real thing
This question is worth 15points
Why do you think that computer programs use different data types? Wouldn't it be simpler if they treated all data the same? Why or why not?
What would happen if, for instance, a date were treated like an integer? Please answer all of the questions.
Answers
Answer:
The data type defines wich operations can safely be performed to create, transform and use the variable in another computation.
Computer programs use different data types for efficiency, precision, etc.
Treating all data the same would lead to confusion, inefficiency, and errors.
Treating a date like an integer would result in a loss of semantics, limited operations, etc.
We have,
Computer programs use different data types for a variety of reasons:
- Efficiency:
Different data types allow programs to allocate memory and perform operations more efficiently.
- Precision:
Different data types have different levels of precision. For example, using floating-point numbers allows for decimal values but might introduce rounding errors, while integers are exact but can't represent fractions.
- Semantics:
Different data types convey meaning and help programmers and the compiler understand how the data should be used.
- Operations:
Different data types support different operations. For instance, you can't perform arithmetic operations on text strings as easily as you can on numbers.
- Type Safety:
Using distinct data types helps catch errors early in the development process. If you accidentally treat a string as an integer or vice versa, type systems can catch such errors during compilation.
If a date were treated like an integer:
- Loss of Semantics:
Treating a date as an integer would strip away its meaning. Dates have attributes like day, month, and year, which would be lost if they were treated as integers.
- Limited Operations:
Integers can't directly perform operations related to date manipulation, such as finding the difference between two dates or determining the day of the week for a given date.
- Error-Prone:
Treating dates as integers would likely lead to confusion and errors. It would be easy to make mistakes when handling date-related calculations and comparisons.
- Lack of Flexibility:
Dates have a complex structure, including leap years, varying month lengths, and time zones. Treating them as integers wouldn't allow for representing these complexities.
Thus,
Computer programs use different data types for efficiency, precision, etc.
Treating all data the same would lead to confusion, inefficiency, and errors.
Treating a date like an integer would result in a loss of semantics, limited operations, etc.
Learn more about computer programs here:
https://brainly.com/question/33841076
#SPJ3
A _______________ is a particular type of network that uses circuits that run over the Internet but that appears to the user to be a private network.
Answers
Answer:
A virtual privte network is a particular type of network that uses circuits that run over the Internet but that appears to the user to be a private network.
Which of the following can be termed “application software”? *
1 point
a) DOS
b) Linux
c) Defragment
d) Internet Explorer/ Microsoft Edge
Answers
The answer option which can be described as an application software is: d) Internet Explorer/ Microsoft Edge.
A software can be defined as a set of executable instructions (codes) that is typically used to instruct a computer on how it should perform a specific task and solve a particular problem.
In Computer and Technology, software applications (programs) are broadly classified into three (3) main categories and these are;
System softwareUtility softwareApplication softwareAn application software refers to a type of software applications (programs) that is typically designed and developed for the performance of a specific task rather than the operation of a computer system. Some examples of application software include the following:
1. Internet Explorer/Microsoft Edge
2. Notepad
3. Windows media player
Find more information: https://brainly.com/question/14379808
The ____ method constructs a text string from Unicode character codes that are passed as arguments.
Answers
Answer:
The fromCharCode() method constructs a text string from Unicode character codes that are passed as arguments.
is invalid in the select list because it is not contained in either an aggregate function or the group by clause.
Answers
Answer:
Column
Explanation:
Discuss the importance of an operating system as it relates to computer hardware and software. Provide at least one example of a service that operating systems provide.
Answers
Answer:
An operating system is the most important software that runs on a computer. It manages the computer's memory and processes, as well as all of its software and hardware. It also allows you to communicate with the computer without knowing how to speak the computer's language.
Examples:
1. User Interface.
2. Program Execution.
3. File system manipulation.
4. Input / Output Operations.
5. Communication.
6. Resource Allocation.
7. Error Detection.
8. Accounting.
How is the central message of being true to oneself conveyed in the story?
Answers
The central message of being true to oneself is illustrated in the story as the character allowed his uniqueness to shine through.
You did not provide the story. Therefore, an overview of the central idea will be given. The central message of a story is the main idea that the author wants the readers to know.
The central message is also referred to as the theme. Since the central message is about being true to oneself, the character will respect the opinions of others but won't conform to stereotypes. Such a person allows their uniqueness to shine through.
Read related link on:
https://brainly.com/question/25582903
why are extensions necessary in scratch programming as a whole?
Answers
una laptop agarra mas internet que una computadora de escritorio?
Answers
una laptop agarra mas internet que una computadora de escritorio?
Su computadora no puede afectar la velocidad de Internet de sus otros dispositivos. ... La única forma en que su computadora puede reducir la velocidad de Internet de otros dispositivos es si no obtiene suficiente velocidad de su ISP y sus dispositivos luchan por un ancho de banda limitado.^^
GUI STANDS FOR__________________
Answers
Explanation:
A graphizaluser interface (GUI) is a type of user interface through which users interact with electronic devices via visual indicator representations.
The secondary storage device that is LEAST portable is a
A. DVD
B. Flash drive
C. Floppy disk
D. Hard disk
Answers
Answer:
B. flash drive
Explanation:
because it is portable
Artificial intelligence (AI) and machine learning are especially important during which security information and event management (SIEM) task?
Answers
Answer:
hueiweke
Explanation:
Artificial intelligence (AI) and machine learning are especially important during analysis and report review security information and event management (SIEM) task. Thus, option (b) is correct.
What is management?
The term “management” refers to the act of managing. The management of the business activities. Management is the basis of art, science, and the profession. Management are they manage the organization. Management are based of the different functions are the step by step.
According to the security information and event management (SIEM) task. There are the artificial intelligence and the learning are the significant review in the information of the task in the management. There was the analysis of the past daily report.
As a result, the artificial intelligence (AI) and machine learning are especially significant during analysis and report review security information and event management (SIEM) task.
Learn more about on management, here:
https://brainly.com/question/29023210
#SPJ2
Your question is incomplete, but most probably the full question was.
A.) Packet capture.B.) Analysis and report review.C.) Data aggregation.D.) Log collection.where is the flash drive listed in a windows 7 save as dialog box?
Answers
Answer:
In the left pane below Computer.
Explanation:
The command used to save a file for the first time and or to save a file with a new file name, location and formatT
Answers
cntrl s dummycntrl s dummycntrl s dummycntrl s dummycntrl s dummy